POWER REDUNDANCY
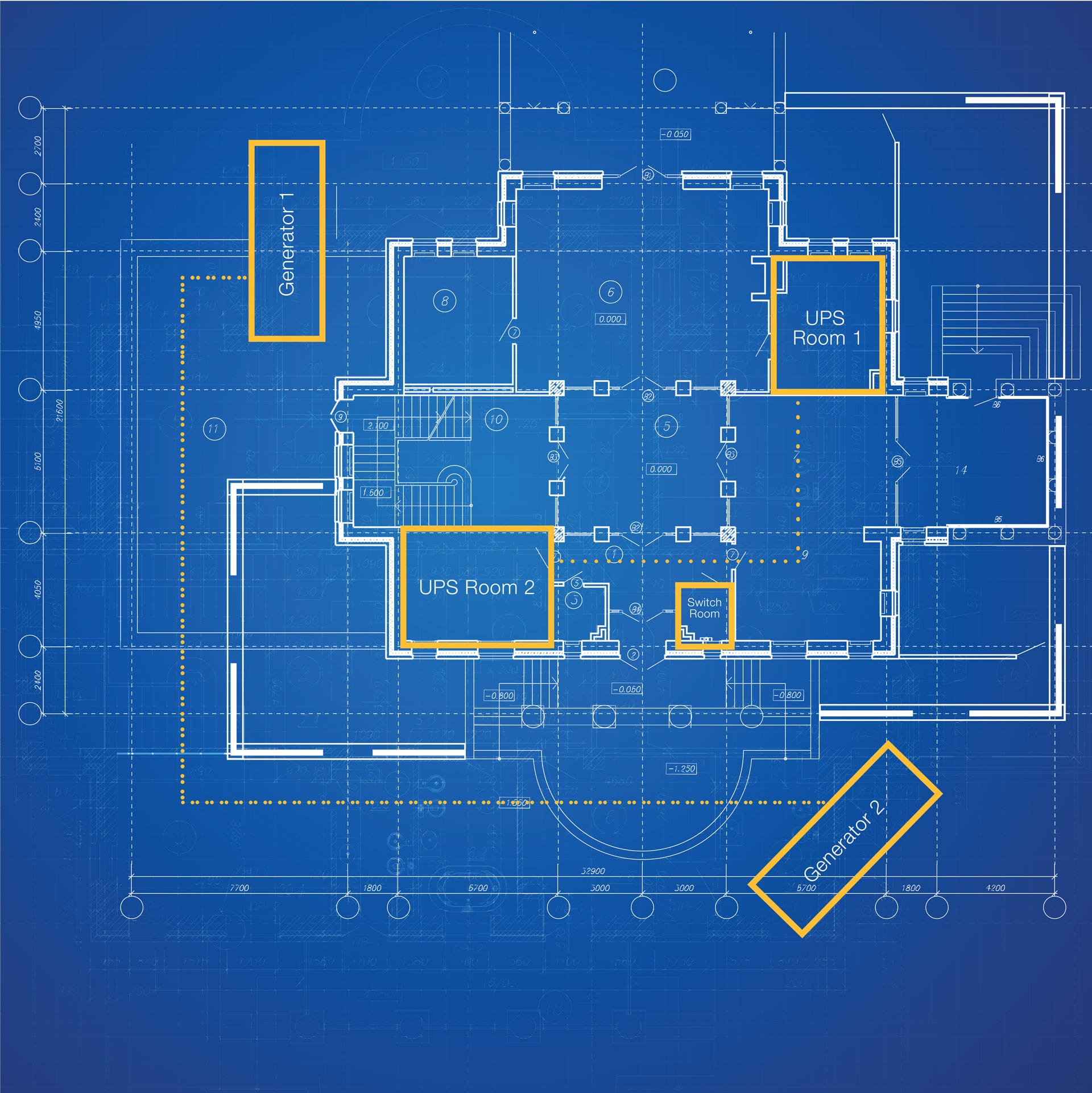
What do remote arctic research stations have in common with Rapid Response? Both use primary generators, not secondary units.
A primary generator is designed, engineered, and built to be the primary source of off-grid power for a facility. A unit like this has the fuel storage, duty rating, and reliability to provide full-time, full-capacity electricity — and we have six of these units supporting our Command Centers.
Through our digitally-controlled CATERPILLAR diesel generators, Rapid Response has enough private power generation at each of our Command Centers to equivalently power 30 homes for 30 days. Power generation is ensured by months of on-site fuel storage in independent redundant tanks.
Electricity runs through multiple enterprise-scale UPS (uninterruptible power supply) battery banks with digital switching controls to eliminate gaps between grid failure and generator spinup. Combined with quad-bus wiring to every piece of equipment in our facilities, power failure is practically impossible.
There’s backup power, and then there’s having powerful backup. That’s the difference of having true redundancy.